Prerequisites
Before configuring RLS, make sure you have the following:- Admin Access: You must have administrator privileges for your WisdomAI domain.
- A Target Table: Identify the table you wish to secure and understand its schema.
- (Optional) Dynamic Filtering Setup: For dynamic RLS, you should have one of the following configured:
- User Attributes: Key-value pairs assigned to users that define their permissions (e.g.,
tenantId: 'abc-123'). Attributes can be set manually by an admin or provisioned automatically via SAML SSO. - Entitlements Table: A dedicated table that maps users to the specific data resources they are allowed to access.
- User Attributes: Key-value pairs assigned to users that define their permissions (e.g.,
Configure RLS on a Table
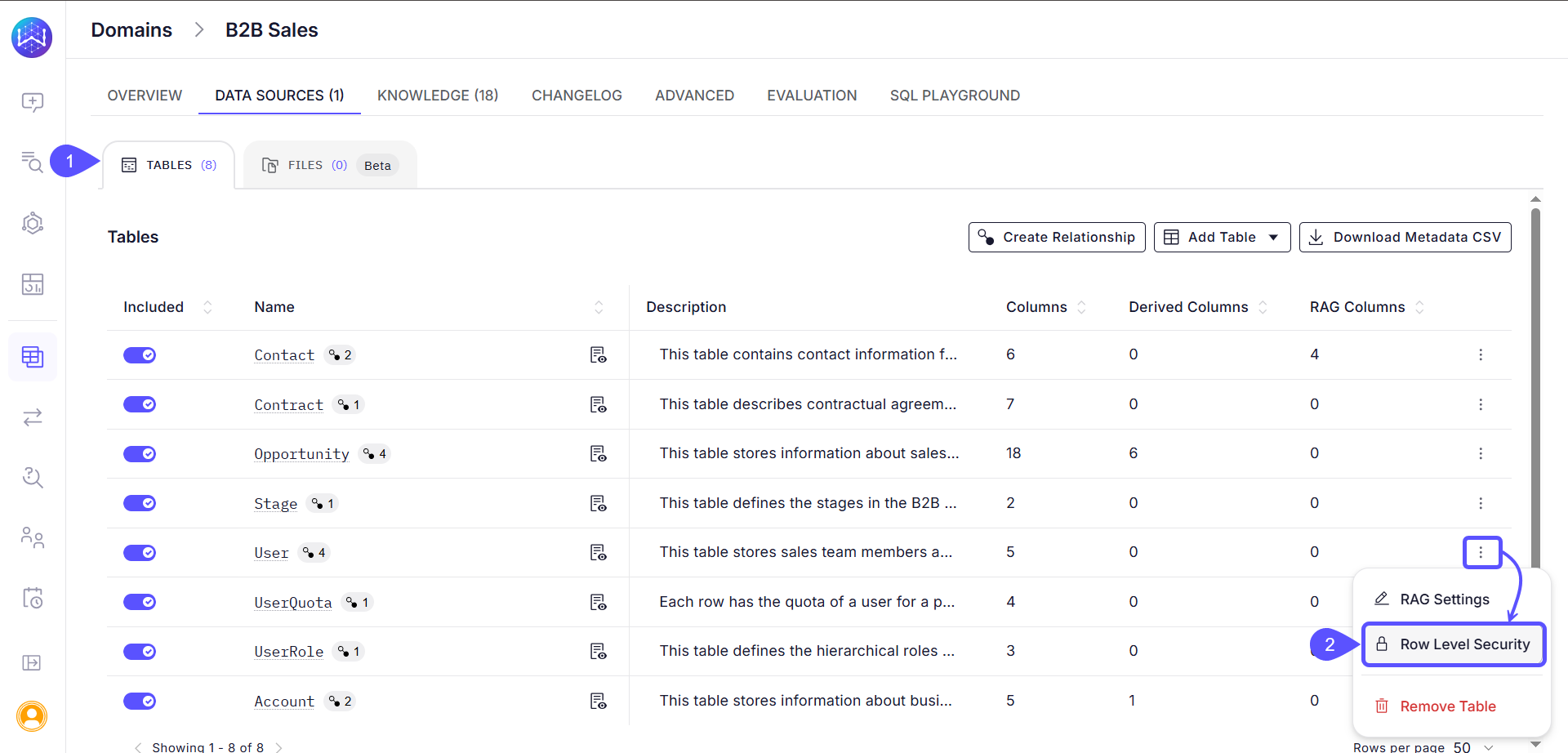
Once your setup is ready, follow these steps to configure row-level security for a table in your WisdomAI domain.- In your WisdomAI domain, navigate to Data > Tables.
- Locate the table you want to secure, click the three-dot menu on the right side of the table row and select Row-Level Security. The Row-Level Security Configuration window will open.
RLS filters are defined as
WHERE clauses that WisdomAI applies to every query on the table. You can define this filter using natural language (recommended) or by writing SQL directly.- Use the Describe Filters text box to explain your access rule in plain language.
- Click Generate. WisdomAI will automatically generate a valid SQL
WHEREclause based on your description, recognizing table columns, user attributes, and entitlements. Here are some examples to help you describe a filter:
| You Type | WisdomAI Generates |
|---|---|
Filter the email column by the current user's email | email = USER_EMAIL() |
Match the tenantId column with the user's tenantId attribute | tenantId = USER_ATTRIBUTE('tenantId') |
Use the entitlements table to filter the territory name | SQL subquery (see below) |
For complex or highly specific rules, you can write the
WHERE clause directly in the SQL text box in a valid SQL syntax. For this, you can use WisdomAI’s built-in functions for dynamic filtering.For a complete list of functions, see Dynamic Filters with Custom Functions.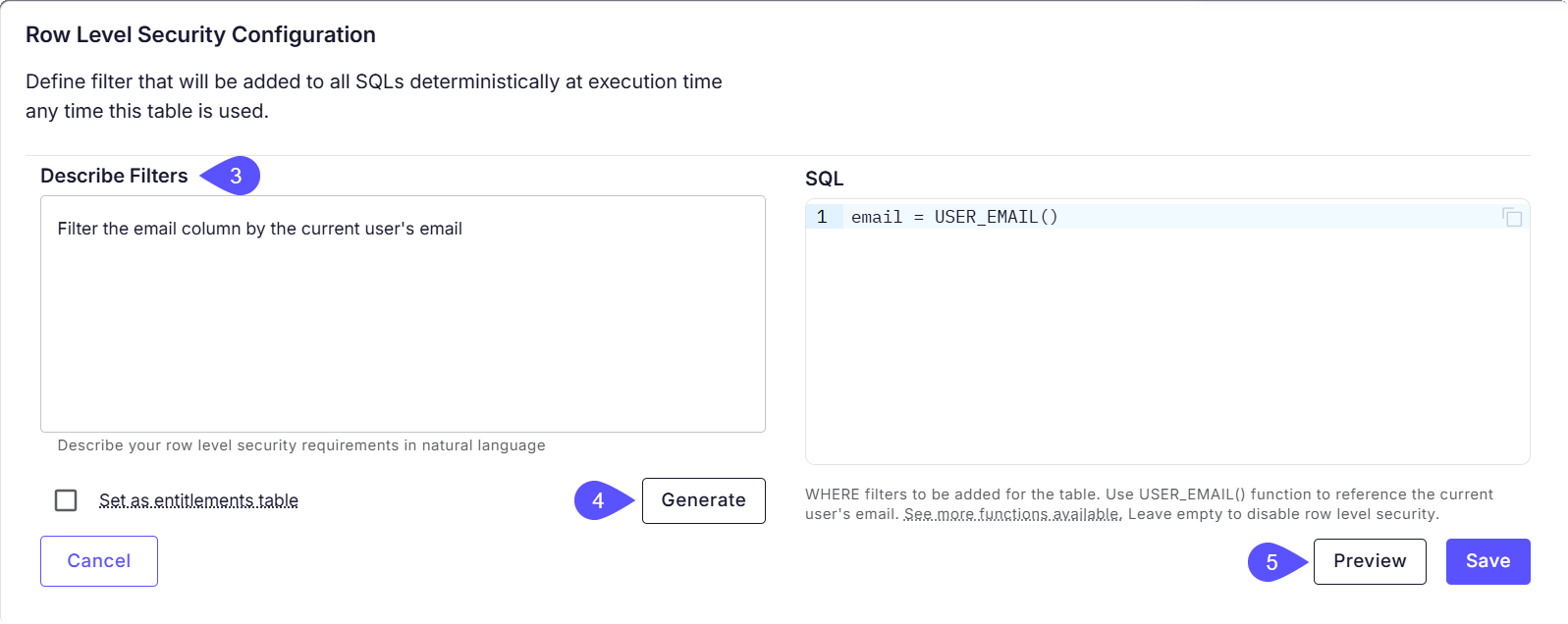
- Click Preview.
- In the Preview Table with Row-Level Security window that opens, locate the Impersonate User field and enter a user’s email address.
- Click Impersonate. The data preview will update to show exactly what that user would see.
- (Optional) Add temporary user attributes to test different scenarios.
- Repeat with different users to validate all access cases.
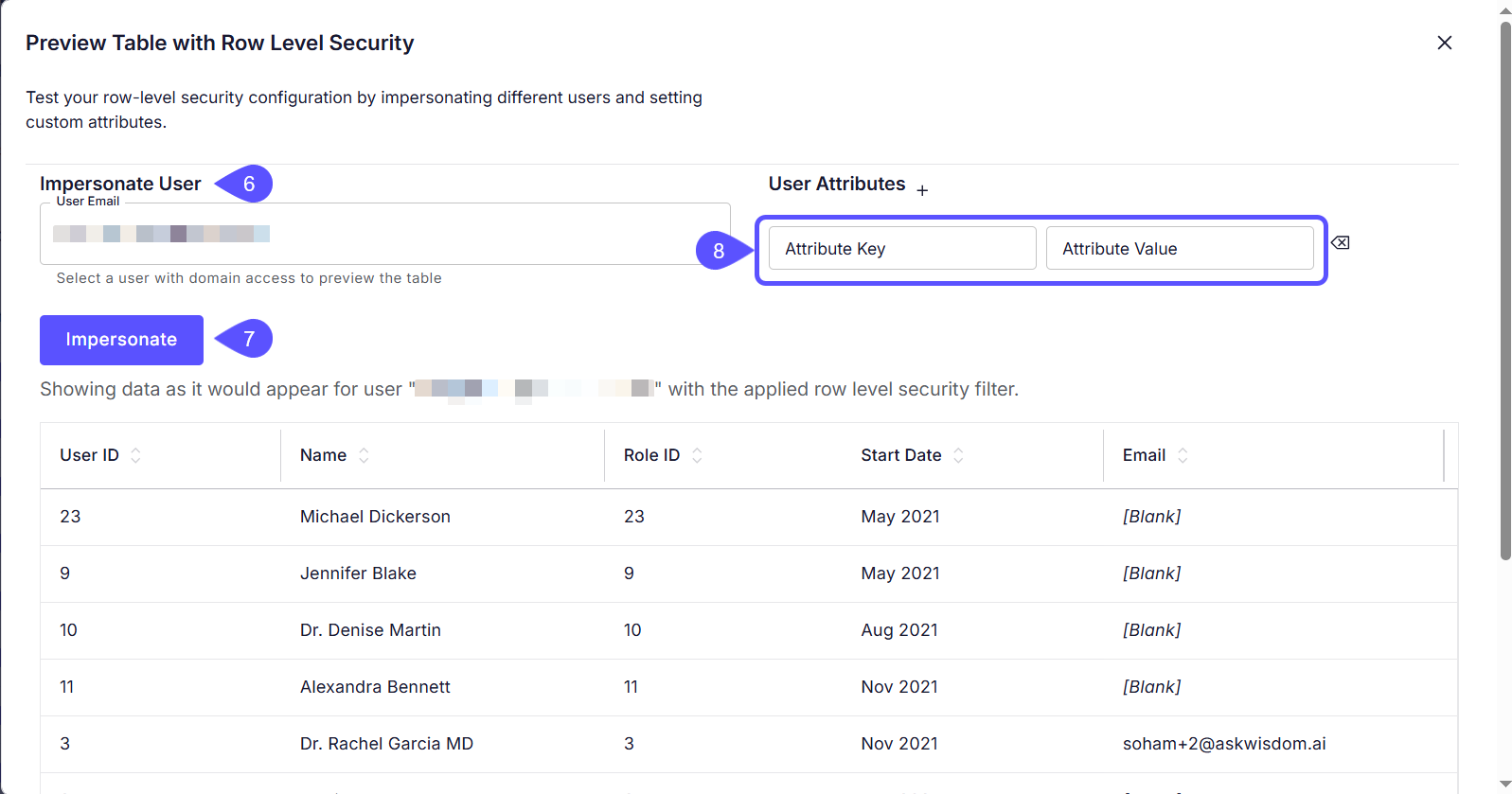
- Once you have verified that the filter works correctly, close the Preview Table with Row-Level Security window and click Save to apply the RLS rule. The filter is now active and will be automatically appended to all queries against this table for non-admin users.
Managing RLS
- To Disable RLS: Open the RLS configuration, clear the contents of the SQL text box, and click Save.
- Applying RLS to Admin Users: By default, admins can see all data. To apply RLS filters to admins as well, enable the corresponding setting in your domain’s Settings > Advanced tab.
- Using a Table as an Entitlements Source: If the table you are securing is itself an entitlements table, check the Set as entitlements table option. This optimizes how WisdomAI uses it for RLS checks on other tables.
Next Steps
Users Management
Manage user roles, permissions, and access to the platform.
Supported Data Sources
Explore the full list of databases and platforms you can connect to the system.
How WisdomAI Works
Understand the core concepts and architecture behind the platform’s data analysis capabilities.
Basic Tutorial: Connect and Test
Walk through the initial setup to connect a data source and run your first query.